SSH Keyboard Authentication. SSH Public Key Authentication. SSH Remote Shell. SSH using SOCKS Proxy. SSH Tunnel (Port Forwarding via direct-tcpip channel) SSH Tunnel with Dynamic Port Forwarding. Multi-Hop SSH (SSH Through SSH) Use PuTTY Key for SSH Authentication. Using sudo in an SSH. Mar 09, 2021 SSH, or Secure Shell, is a remote administration protocol that allows users to control and modify their remote servers over the Internet. The service was created as a secure replacement for the unencrypted Telnet and uses cryptographic techniques to ensure that all communication to and from the remote server happens in an encrypted manner. As of April 12, 2019, SSH keys are required when SSHing to CS/CSRES networks when outside of our networks, campus wireless, or the VPN. The University ISO will quarantine any host allowing SSH access that has not disabled password authentication. An SSH key pair consists of two keys: One public key and one private key. SSH.COM is one of the most trusted brands in cyber security. We help enterprises and agencies solve the security challenges of digital transformation with innovative access management solutions. About SSH.COM Popular. Gartner on Zero Standing Privileges PrivX - watch how it works.
Table of Contents

- Overview
- Connect to your server via SSH
- Manage SSH keys
- Generate a New Key
- Import Key
- Manage your keys
Table of Contents
- Overview
- Connect to your server via SSH
- Manage SSH keys
- Generate a New Key
- Import Key
- Manage your keys
SSH Access
Valid for versions 82 through the latest version
Last modified: February 23, 2021
Overview
This interface provides information about how to connect to another web server via the SSH (secure shell) network protocol.
The SSH network protocol allows you to connect to another web server over the internet via a command line interface (CLI). You can use this network protocol to remotely manage your server, configure CGI scripts, and perform other tasks.
Many modern operating systems, such as macOS® and Linux® distributions, include SSH. If you use Microsoft Windows® to connect to your server, you must use an SSH client, such as PuTTY, to log in to your server.
Many Unix-based operating systems include standardized commands. For a list of standardized Unix-based (POSIX) commands, read the GNU Coreutils documentation.

Connect to your server via SSH
To use PuTTY to connect to your server via SSH, perform the following steps:
Download and install the PuTTY client.
From the Windows Start menu, open the client.
In the Session interface, enter the hostname or IP address of the server in the Host Name (or IP address) text box (for example,
192.0.2.0).Enter the port number in the Port text box (for example,
22).Select the SSH protocol.
Click Open.
Enter your cPanel account’s username.
Enter your cPanel account’s password.
To log in to a server via SSH with PuTTY and a public key, perform the following steps:
From the Windows Start menu, open the client.
Navigate to the PuTTY Key Generator interface.
Under the Actions heading, click Generate. PuTTY will generate the key and display the result under the Key menu.
Copy the public key and paste it in the
.ssh/authorized_keysfile.Enter a passphrase in the Key passphrase and Confirm passphrase text boxes.
Click Save private key and save the key as a
.ppkfile.In the Session interface, from the Saved Sessions menu, select your preferred authorization session and click Load.
Navigate to the Auth interface under the SSH category.
Click Browse, select the private key file to upload, and click Open.
Navigate to cPanel’s Manage SSH Keys interface (Home >> Security >> SSH Access >> Manage SSH Keys) and import the server’s keys.
C Sharp
Log in with a Password
To log in to your server with a password via SSH using macOS or Linux, perform the following steps:
Open a Terminal session.
Run the following command:
ssh -p port user@IPwhereportrepresents the port number,userrepresents your username, andIPrepresents your IP address. For example:Enter your password.
The password login process is similar to the following example:
Log in with a SSH Key
To log in to your server with a password via SSH using macOS or Linux, perform the following steps:
Open a Terminal session.
Run the following command:
ssh -p port -i ssh-key user@IPwhereportrepresents the port number,ssh-keyrepresents the file path to your SSH key,userrepresents your username, andIPrepresents your IP address. For example:Enter your SSH key password. If you did not set a password when you created the SSH key, press Enter when the system prompts you for a password.
The SSH Key login process is similar to the following example:
Manage SSH keys
This section of cPanel’s SSH Access interface allows you to create, import, manage, and remove SSH keys. The system will use these keys when you confirm that a specific computer has the right to access your website’s information with SSH.
Generate a New Key
Use this section of the interface to create new SSH key pairs, which include a public key and a private key.
To generate a new SSH key pair, perform the following steps:
Click Manage SSH Keys.
Click Generate a New Key.
To use a custom key name, enter the key name in the Key Name (This value defaults to id_rsa): text box.
If you use a custom key name, you must manually specify the SSH key when you log in to the server.Enter and confirm the new password in the appropriate text boxes.
- This step is optional if your hosting provider sets the SSH Keys setting to
0in WHM’s Password Strength Configuration interface (WHM >> Home >> Security Center >> Password Strength Configuration). - The system evaluates the password that you enter on a scale of 100 points.
0indicates a weak password, while100indicates a very secure password. - Some web hosts require a minimum password strength. A green password Strength meter indicates that the password is equal to or greater than the required password strength.
- Click Password Generator to generate a strong password. For more information, read our Password & Security documentation.
- This step is optional if your hosting provider sets the SSH Keys setting to
Select the desired key type.
DSA keys provide quicker key generation and signing times.
RSA keys provide quicker verification times.
Select the desired key size.
Greater key sizes provide more security, but they result in larger file sizes and slower authentication times.Click Generate Key. The interface will display the saved location of the key.
For the new SSH key to function, you must authorize the SSH key. For more information, read the Manage your keys section.
Import Key
To import an existing SSH key, perform the following steps:
Click Manage SSH Keys.
Click Import Key.
To use a custom key name, enter the key name in the Choose a name for this key (defaults to id_dsa) text box.
If you use a custom key name, you must manually specify the SSH key when you log in to the server.Paste the public and private keys into the appropriate text boxes.
Click Import.
Manage your keys
The Public Keys and Private Keys tables display the following information about your existing keys:
Name — The key’s name. Public and private keys use the same key name.
Authorization Status — Whether you authorized the key.
You must authorize new keys before you attempt to use them.This column only displays in the Public Keys table.Actions — You can perform the following actions:
Delete Key — Click to delete the key, and then click Yes to confirm that you wish to delete the key.
View/Download — Click to view or download the key. To download the key, save the contents of the Public SSH Key text box to your computer.
Manage — Click to manage authorization for the key. A new interface will appear. Click Authorize to authorize the key, or Deauthorize to revoke authorization for the key.
You can only perform this action for public keys.
After you deauthorize a key, that key’s users cannot log in with the associated private key.
Additional Documentation
Table of contents
- Copying your key to a server
These notes are for Windows 10 only. If you find that you don't have the 'ssh' command, please ensure that you have all of the latest updates applied to your system. You can do so by selecting the Start button, then going to Settings > Update & Security > Windows Update, then selecting Check for updates.
For instructions on adding SSH keys for other platforms, visit this FAQ.
Introduction
As of April 12, 2019, SSH keys are required when SSHing to CS/CSRES networks when outside of our networks, campus wireless, or the VPN. The University ISO will quarantine any host allowing SSH access that has not disabled password authentication.
An SSH key pair consists of two keys: One public key and one private key. The public key, as the name suggests, is public and can be safely shared with the world. The private key should never be shared with anyone and should be kept safe.
In order to use SSH keys to connect to a remote computer, one must first create an SSH key pair on one's computer, then copy the public SSH key to the remote computer. You will create an SSH key pair on each computer that you want to SSH from. You can use the same public SSH key from one computer to connect to many others.
E.g., if you have two computers at home, home1 and home2, and want to use them to connect to remote1, remote2, and remote3 you would create an SSH key pair on both home1 and home2, and then send the public key from home1 to all three remote computers, and lastly you would send the public key from home2 to all three remote computers.
Ssh C Command

Below are the necessary instructions to create an SSH key pair and add your public key to your CS account. Adding your public SSH key to linux.cs.utexas.edu will automatically add it to all other machines on the CS network. For the purposes of these instructions, we will assume that you want to SSH into a CS machine from a computer at home. To avoid confusion, we will use the following terminology:
HOME = Your home computer
CS_USER = Your CS username
linux.cs.utexas.edu = The machine that you need to SSH into and add SSH key to.
NOTE: All commands will be run on HOME.
Open a CMD prompt
Firstly, you will want to open a CMD prompt in which you will type all of the commands in the next steps. To do so, simply:
- Hold the Windows key and press
r. This will open the 'Run' window. - Type
cmdand press Enter (or click 'OK').
You will now have a black CMD prompt waiting for your input.
Creating a key
To create a 4096-bit RSA key, run the following:
ssh-keygen -t rsa -b 4096- Press Enter to use the default location. (Recommended) 1
- Enter a passphrase (ALWAYS use a passphrase!!) 23
- Enter your passphrase a second time.
It should look something like this:
Your public SSH key is located by default at C:Users<username>.sshid_rsa.pub and is perfectly safe to be shared with anyone.
Your private SSH key will be located by default at C:Users<username>.sshid_rsa. You should NOT touch this file or share it with anyone.
Copying your key to a server
From UT VPN, UT wireless, or CS network
If you are connected to UT VPN, or have brought your machine on campus and have connected to UT wireless or the CS network, then you can use the method below.
You can find more information on how to connect to UT VPN by visiting this page.
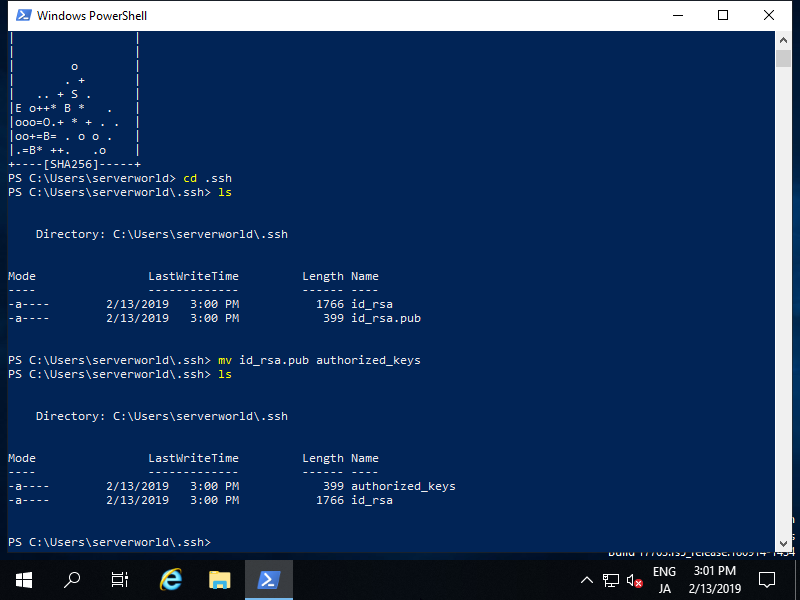
To copy your SSH public key from HOME to linux.cs.utexas.edu, simply copy and paste the below command into a CMD prompt:
type .sshid_rsa.pub | ssh CS_USER@linux.cs.utexas.edu 'umask 0077 && mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys'- If you see the text 'Are you sure you want to continue connecting (yes/no)?' type
yesand press Enter. - Enter CS_USER's password to send your public key to the server.
- If successful, you will not see any special output. It will go back to the normal CMD prompt with a blinking cursor.
Congratulations! You can now use your SSH key to log into any CS machine that you have access to!
From off-campus
Copy to a USB drive
If you are unable to connect to UT VPN or cannot bring your machine to campus, then copying your public SSH key to a USB drive is another solution.
On your home computer:
- Plug in a USB drive.
- If it does not auto-mount, open a file manager and open the USB device to view its contents.
- Open another File Explorer window and navigate to
C:Usersyourusername.ssh. - Copy the
id_rsa.pubfile to your USB's folder. - Safely unmount/eject your USB drive and bring it to campus.
From here, you will want to log into a CS lab machine and do:
- Plug in the USB drive
- If it does not auto-mount, open a file manager and open the USB device to view its contents.
- In a terminal, run
df -hTto find the full path to your mounted USB drive. cat /media/yourusername/directory/id_rsa.pub >> ~/.ssh/authorized_keys(Replace the second path with your real USB drive's mount point path)chmod 700 ~/.ssh && chmod 600 ~/.ssh/authorized_keys- If step #5's command gives any errors, please submit a helpreq.
- Safely unmount/eject your USB drive.
Using ssh-agent (optional)
ssh-agent is a program included in OpenSSH that will remember your SSH key and not require you to type its passphrase each time you use SSH. Your desktop environment on HOME should start up ssh-agent when you log in.
- Hold the Windows key and press
r. This will open the 'Run' window. - Type
services.mscand press Enter (or clickOK). - Scroll through the list of services until you find 'OpenSSH Authentication Agent'.
- Right-click on 'OpenSSH Authentication Agent' and select 'Properties'.
- Under 'Startup type', choose 'Automatic'.
- Click 'Apply'.
- Click the 'Start' button underneath 'Service status'.
- Click 'OK' to complete this process and close the Services window.
From here the SSH Authentication agent is running and you can now use the ssh-agent command to have Windows securely remember your SSH private key's passphrase.
To add your SSH key to the agent, simply type:
ssh-addType in your SSH key's passphrase and you're good to go!
You won't need to type in your passphrase or even ssh-agent any longer, even after a reboot. You can simply use your normal ssh commands.
Additional information
If you choose to not use the recommended location for your private key, you will need to specify its location in either your
sshcommand (with -i) or after yourssh-addcommand if using ssh-agent.↩This is not your CS_USER's password. The passphrase that you choose for your SSH key should be different from your CS_USER's password. See Selecting a strong password to learn how to choose a secure passphrase instead of a password.↩
When typing your passphrase, you won't see any output on your screen. This is normal and is for your security.↩
