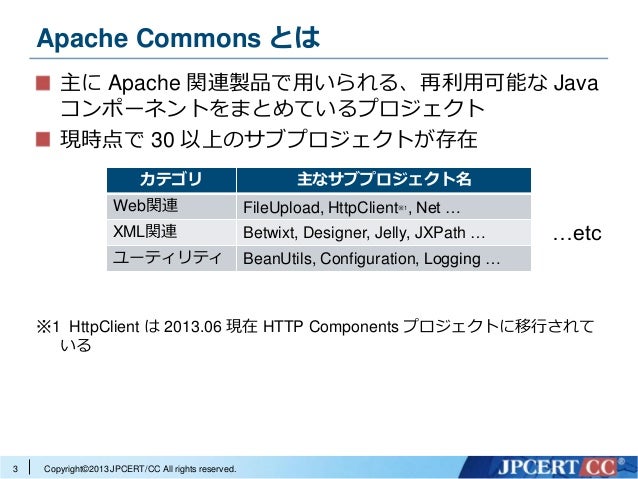
OCSP Stapling
Check through your httpd.conf file, by default in “C: Program Files Apache Software Foundation Apache conf ” and remove the hash (#) tags on the following lines: LoadModule sslmodule modules/modssl.so Include conf/extra/httpd-ssl.conf. Upon further investigation, our request client has a socket timeout of 30 seconds, whereas the socket created by the SSLConnectionSocketFactory has a request timeout of 0. The Commons HttpClient project is now end of life, and is no longer being developed. It has been replaced by the Apache HttpComponents project in its HttpClient and HttpCore modules, which offer better performance and more flexibility.
The Online Certificate Status Protocol (OCSP) is a mechanism fordetermining whether or not a server certificate has been revoked, and OCSPStapling is a special form of this in which the server, such as httpd andmod_ssl, maintains current OCSP responses for its certificates and sendsthem to clients which communicate with the server. Most certificatescontain the address of an OCSP responder maintained by the issuingCertificate Authority, and mod_ssl can communicate with that responder toobtain a signed response that can be sent to clients communicating withthe server.
Because the client can obtain the certificate revocation status fromthe server, without requiring an extra connection from the client to theCertificate Authority, OCSP Stapling is the preferred way for therevocation status to be obtained. Other benefits of eliminating the communication between clients and the Certificate Authority are that theclient browsing history is not exposed to the Certificate Authority andobtaining status is more reliable by not depending on potentially heavilyloaded Certificate Authority servers.
Because the response obtained by the server can be reused for all clientsusing the same certificate during the time that the response is valid, theoverhead for the server is minimal.
Once general SSL support has been configured properly, enabling OCSPStapling generally requires only very minor modifications to the httpdconfiguration — the addition of these two directives:
These directives are placed at global scope (i.e., not within a virtualhost definition) wherever other global SSL configuration directives areplaced, such as in conf/extra/httpd-ssl.conf for normal open source builds of httpd, /etc/apache2/mods-enabled/ssl.conffor the Ubuntu or Debian-bundled httpd, etc.
The path on the SSLStaplingCache directive(e.g., logs/) should match the one on the SSLSessionCache directive. This path is relativeto ServerRoot.
This particular SSLStaplingCache directive requiresmod_socache_shmcb (from the shmcb prefix on thedirective's argument). This module is usually enabled already forSSLSessionCache or on behalf of some module other thanmod_ssl. If you enabled an SSL session cache using a mechanism other than mod_socache_shmcb, use that alternativemechanism for SSLStaplingCache as well. For example:
You can use the openssl command-line program to verify that an OCSP responseis sent by your server:
The following sections highlight the most common situations which requirefurther modification to the configuration. Refer also to the mod_ssl reference manual.
If more than a few SSL certificates are used for the server
OCSP responses are stored in the SSL stapling cache. While the responsesare typically a few hundred to a few thousand bytes in size, mod_ssl supports OCSP responses up to around 10K bytes in size. With more than a few certificates, the stapling cache size (32768 bytes in the example above) may need to be increased. Error message AH01929 will be logged in case ofan error storing a response.
If the certificate does not point to an OCSP responder, or if adifferent address must be used
Refer to the SSLStaplingForceURL directive.
You can confirm that a server certificate points to an OCSP responderusing the openssl command-line program, as follows:

If the OCSP URI is provided and the web server can communicate to itdirectly without using a proxy, no configuration is required. Note thatfirewall rules that control outbound connections from the web server mayneed to be adjusted.
If no OCSP URI is provided, contact your Certificate Authority todetermine if one is available; if so, configure it withSSLStaplingForceURL in the virtualhost that uses the certificate.
If multiple SSL-enabled virtual hosts are configured and OCSPStapling should be disabled for some
Add SSLUseStapling Off to the virtual hosts for which OCSPStapling should be disabled.
If the OCSP responder is slow or unreliable
Several directives are available to handle timeouts and errors. Referto the documentation for theSSLStaplingFakeTryLater,SSLStaplingResponderTimeout, andSSLStaplingReturnResponderErrorsdirectives.
If mod_ssl logs error AH02217
In order to support OCSP Stapling when a particular server certificate isused, the certificate chain for that certificate must be configured. If it was not configured as part of enabling SSL, the AH02217 error will be issuedwhen stapling is enabled, and an OCSP response will not be provided for clientsusing the certificate.
Refer to the SSLCertificateChainFileand SSLCertificateFile for instructionsfor configuring the certificate chain.
- Apache HttpClient Tutorial
- Apache HttpClient Resources
- Selected Reading
Using the HttpClient library you can send a request or, login to a form by passing parameters.
Follow the steps given below to login to a form.
Step 1 - Create an HttpClient object
The createDefault() method of the HttpClients class returns an object of the class CloseableHttpClient, which is the base implementation of the HttpClient interface. Using this method, create an HttpClient object −
Step 2 - Create a RequestBuilder object
The class RequestBuilder is used to build request by adding parameters to it. If the request type is PUT or POST, it adds the parameters to the request as URL encoded entity
Create a RequestBuilder object (of type POST) using the post() method.
Step 3 - Set Uri and parameters to the RequestBuilder.
Set the URI and parameters to the RequestBuilder object using the setUri() and addParameter() methods of the RequestBuilder class.
Step 4 - Build the HttpUriRequest object
After setting the required parameters, build the HttpUriRequest object using the build() method.
Step 5 - Execute the request

The execute method of the CloseableHttpClient object accepts a HttpUriRequest (interface) object (i.e. HttpGet, HttpPost, HttpPut, HttpHead etc.) and returns a response object.
Execute the HttpUriRequest created in the previous steps by passing it to the execute()method.
Example
Following example demonstrates how to logon to a form by sending login credentials. Here, we have sent two parameters − username and password to a form and tried to print the message entity and status of the request.
Output
On executing, the above program generates the following output −
Form Login with Cookies
If your form stores cookies, instead of creating default CloseableHttpClient object.
Create a CookieStore object by instantiating the BasicCookieStore class.
Create a HttpClientBuilder using the custom() method of the HttpClients class.
Set the cookie store to the client builder using the setDefaultCookieStore() method.
Build the CloseableHttpClient object using the build() method.
Build the HttpUriRequest object as specified above by passing execute the request.
If the page stores cookies, the parameters you have passed will be added to the cookie store.
You can print the contents of the CookieStore object where you can see your parameters (along with the previous ones the page stored in case).
Apache Httpclient Ssl
To print the cookies, get all the cookies from the CookieStore object using the getCookies() method. This method returns a List object. Using Iterator, print the list objects contents as shown below −
